How we do personal cyber security threat modeling
21 Nov 2022 - Justin Higgins
Threat modeling forms the core of the process we follow with each of our customers. We needed a process that is flexible enough to be adapted for each customer's needs but provides a framework to ensure we consistently cover all of the angles and are able to show a solid justification for each of our recommendations.
These recommendations should be:
- Proportionate to the threats our customer faces
- Hyper specific to their devices and situation
- As non-disruptive to their workflow as possible
- Fully explained and easy to implement
- Sustainable in terms of effort, cost and security updates
Meet with the customer
We meet with the customer to find out more about them, their concerns and situation. We help the customer answer the five questions posed by the EFF's security plan guidance:
- What do I want to protect?
- Who do I want to protect it from?
- How bad are the consequences if I fail?
- How likely is it that I will need to protect it?
- How much trouble am I willing to go through to try to prevent potential consequences?
These questions help frame the conversation and allow to drill down into the area where we need concrete information to use for threat modeling:
Service & Device details
This includes writing down a simple list of all of the devices they use, as well running some basic software and configuration inventory scripts on their devices to find out as much about them as possible.
Sensitive Data Assets
Now that we have a rough idea of what kind of work the customer does and where they store their data, we can start talking about which information they store would have the largest impact if it was lost, leaked or tampered with. As well as stored data, these assets might also include information that they don't explicitly produce and store like physical location history, social media activity and their conversations
Likely Adversaries
This section is usually the most speculative. Although we will prompt the customer with information about how someone could potentially attack them for some kind of monetary or legal reasons, there is a lot of social and legal context needed to determine who your adversaries and ultimately it's the customer and their knowledge of their own environment that decides who their likely adversaries are.
Service & device research
The other major component of the background information we need is the technical information for each of the components in our customer's setup. We get some of this information from inventory and information gathering during discussion with the customer, but we need to do research to get all of the finer details.
Services
We look to answer the following questions to determine the security posture of a service:
- What security standards does the service provider purport to maintain?
- Do they have a privacy policy?
- Where are their corporate offices situated?
- What information can we find out about their hosting? Where are they hosted? Do they self-host? Do they use a cloud provider? Do they use a CDN?
- Has there been any past history of security incidents for this service?
Devices
Our research process for devices is similar to services, but with more of a focus on technical detail:
- What vulnerabilites (CVEs) have been disclosed in the past for this device?
- What OS does it run? What CPU architecture?
- What communication protocols does it use?
- Does it have any security features that can be enabled?
- Does this device have secure default settings? Is there a hardening guide available?
OSINT
With our customer's permission, we use standard OSINT techniques to check our customers's social media accounts, see what information they have published, check their permissions settings and generally search for any information that might be useful to their adversaries
Attack trees
Now we have the background information for our customer, we use a variant of Bruce Schneier's Attack Tree method of analysis to examine what vectors an adversary could use to attack the sensitive information assets our customer has.
IRL Cyber maintains a database of potential attack vendors and how they relate to different classes of attackers and customer services and devices. We filter these vectors based on what we know about our customer's situation and then use those vectors to populate an attack tree for each information asset.
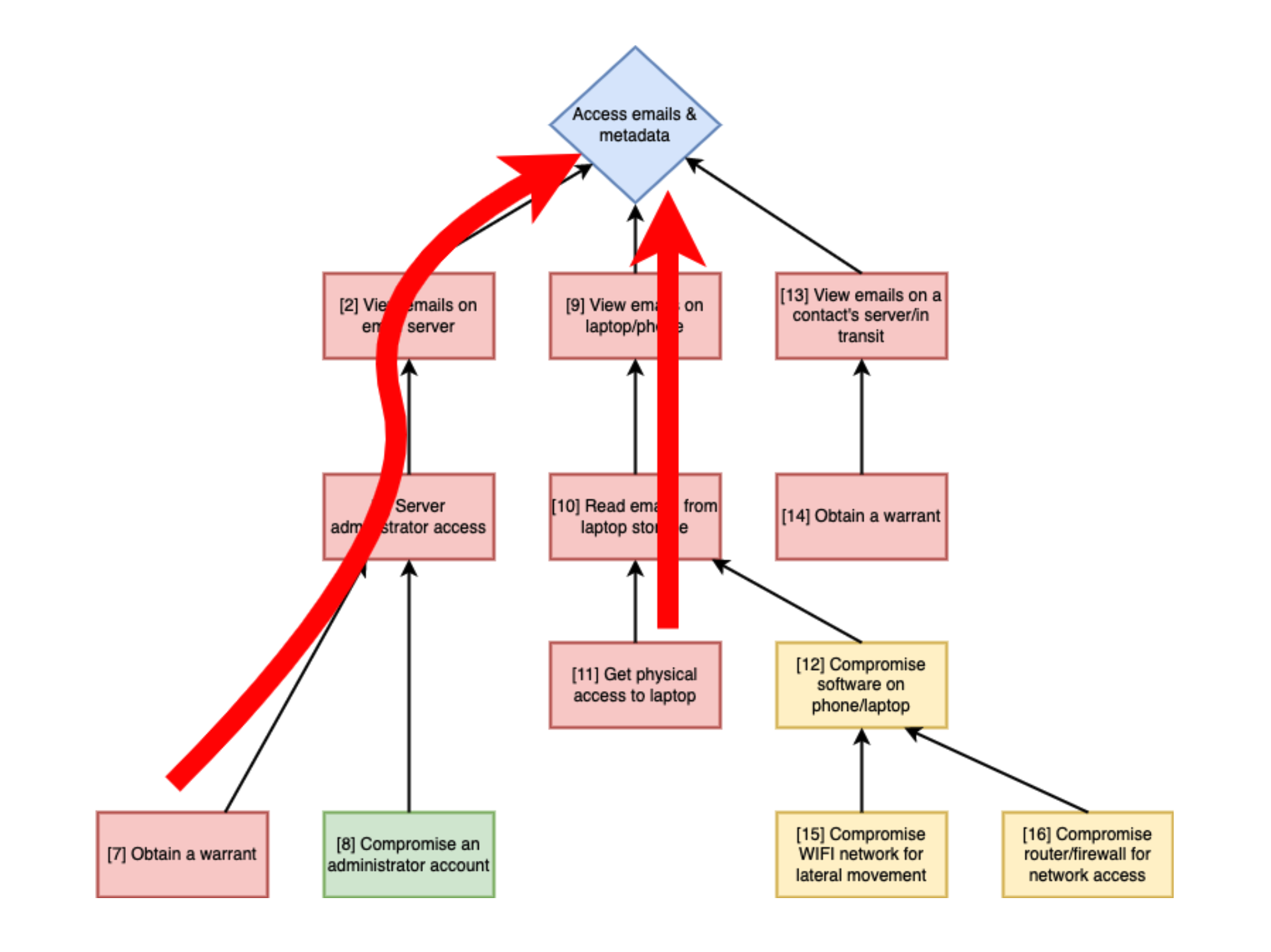
For each of the vector nodes in the attack trees we examine the information we have for the customer and determine if the vector:
- is already mitigated (green)
- is viable, but will be mitigated if our recommendations are implemented (orange)
- is viable, with no known countermeasure if use of this device/service continues (red)
At that point we can trace paths up the attack trees (see large red arrow above) and see if there are any relevant attack vectors with no known counters. This allows us to draw conclusions about whether this customer should continue using a particular technology and how critical a recommendation is. We record all of our analysis for each node to be delivered to the customer for reference.
Recommendations
Finally we are ready to write the advice that our customer will actually read! We document the recommendations in an easy-to-understand format and then discuss them with the customer to see which recommendations they would like to implement and to ensure they understand the implications of following/ignoring each recommendation. We then write instructions for the customer explaining how they can implement each recommendation. Customers then have the option of implementing the recommendations by themselves, or booking time with us to walk them through the steps if they're less confident.
That's it!
Our process can be quite involved for some customers, but we want to give them the best possible advice, so we think it's worth it.
What do you think? Have you thought about your own security situation this way before? Are you a security professional that uses a different method?
Tweet at us on everyone's favourite social network and let us know